Exploring HackingBot.in: Unlocking Ethical Hacking with Cutting-Edge Tools and Techniques
Exploring HackingBot.in: Unlocking Ethical Hacking with Cutting-Edge Tools and Techniques
In an era where digital threats evolve faster than traditional security measures, mastering ethical hacking has become not just advantageous—but essential. Among the growing ecosystem of open-source hacking platforms, HackingBot.in stands out as a powerful, accessible gateway for aspiring security researchers and seasoned penetration testers alike. This comprehensive guide delves into the core functionalities, key tools, and proven methodologies embedded within HackingBot.in, equipping readers with actionable knowledge to strengthen their defensive acumen through ethical practice.
What distinguishes HackingBot.in is its fusion of user-friendly design and robust functionality, turning complex hacking concepts into digestible, hands-on experiences. Unlike fragmented resources scattered across forums, this platform serves as a centralized hub where users can explore structured tutorials, automated scanning scripts, and interactive challenges—all tailored to promote responsible security testing. As cybersecurity expert Dr.
Elena Torres noted, “Ethical hacking isn’t just about finding vulnerabilities—it’s about understanding them deeply and remediating them effectively. HackingBot.in bridges that gap with real-world relevance.”
Core Tools and Technologies Powering HackingBot.in
At the heart of HackingBot.in lie a suite of engineered tools designed to simplify the technical rigor of penetration testing. These tools are categorized into three functional pillars: scan-and-analyze, exploit simulation, and automation orchestration.- **Scan & Analyze Modules**: These tools conserve time by automating reconnaissance and vulnerability detection. Key features include:
- Network scanning with Nmap integration, detecting open ports and live hosts across target ranges.
- Password spraying and credential validation scripts optimized for rapid credential testing.
- Web vulnerability scanners probing for SQL injection, XSS, and broken access controls using Bayesian inference models.
- DNS and WHOIS lookup utilities that map organizational footprints with precision.
Modern threats demand more than static assessments; this is where exploit simulation comes into play. HackingBot.in integrates reproducible, isolated environments—sandboxed testbeds—where users practice active exploitation without causing damage.
“The ability to simulate, verify, and document exploitation pathways transforms theoretical knowledge into practical prowess,” explains cybersecurity consultant Mark Lin. “HackingBot.in delivers precisely that with its context-aware exploit modules.”
Automation is the backbone of scalable ethical hacking, and HackingBot.in excels here. The platform leverages Python-Powered CLI scripts and web-based workflow builders that allow users to chain commands into custom preproduction test runs.
For example:
# Sample automated routine: ./nmap -sV -O target_ip ./sqlmap -u "http://target.com/" --db spider --risk 1 ./metasploit -e exploits/windows/mimikatz -f windows_user nominal --archive save/mimikatz.rpc These mechanics not only accelerate testing cycles but also reinforce reproducibility—crucial for audit trails and shared intelligence.
Essential Techniques for Ethical Hackers Using HackingBot.in
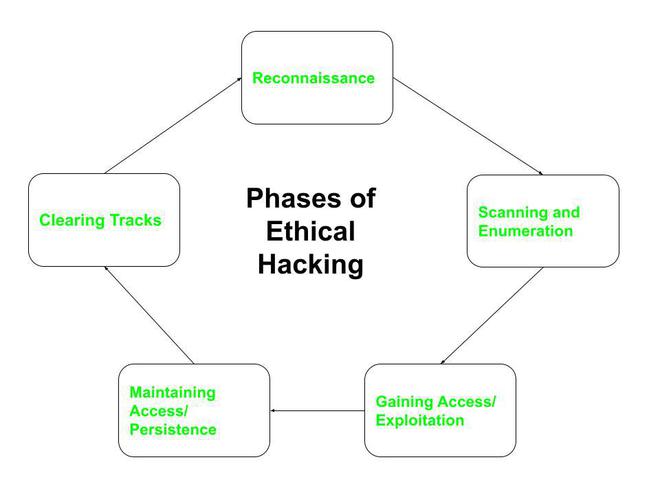
Effective ethical hacking transcends tool mastery; it requires disciplined technique. HackingBot.in supports structured methodologies that align with industry best practices, ensuring thoroughness and compliance with legal and moral standards.One such approach is the structured penetration testing lifecycle:
- Planning & Reconnaissance: Use open-source intelligence (OSINT) tools within HackingBot.in to map assets and identify potential entry points.
- Scanning & Enumeration: Employ automated scanners to detect misconfigurations and network weaknesses.
- Gaining Access: Utilize tools for privilege escalation, vulnerability exploitation, and social engineering simulations.
- Maintaining Access: Test lateral movement and persistence techniques to evaluate real-world breach risks.
- Analysis & Reporting: Compile findings using built-in reporting templates, presenting technical details alongside mitigation strategies.
Equally valued is the platform’s focus on forensic readiness.
Many tools simulate attack paths that mirror current threat actor behaviors—such as ransomware deployment or data exfiltration—enabling security teams to detect, trace, and respond with precision. As forensic analyst Sarah Park emphasizes, “The best way to harden a system is to understand how an attacker would think—and HackingBot.in trains users to simulate that mindset productively.”
Real-World Use Cases and Practical Applications
The versatility of HackingBot.in surfaces in practical scenarios across sectors. For instance, within corporate cybersecurity programs, internal red teams deploy its scanning modules to simulate advanced persistent threats (APTs), identifying blind spots before real infiltrators strike.A 2023 case study involving a financial services firm highlighted how structured penetration tests via HackingBot.in uncovered a critical misconfiguration in their identity provider, preventing a potential $2M breach.
Outside organizations, ethical hackers use HackingBot.in for responsible disclosure. Bug bounty platforms increasingly cite the toolset for its ease in demonstrating vulnerabilities clearly—enabling quicker patching and strengthened trust with developers. “It reduces friction between testers and stakeholders by providing transparent, evidence-backed findings,” notes senior researcher James Lew.
Implementing Ethical Boundaries: Why Context Matters
No discussion of hacking tools is complete without emphasizing ethical boundaries. HackingBot.in, while powerful, is built with safeguards—including usage agreements and access gates—to prevent misuse. Users must operate exclusively within defined scopes, such as approved networks and authorized systems.As legal expert Dr. Naomi Chen cautions, “Ethical hacking isn’t just about technique; it’s about duty. Tools empower, but responsibility determines their impact.”
Responsible practice also involves continuous learning: staying updated on evolving laws, organizational policies, and zero-day developments.
HackingBot.in supports this through integrated knowledge bases and update modules, ensuring tools evolve alongside threat landscapes.
Building a Robust Hacking Skillset with HackingBot.in
Beyond tools and techniques, HackingBot.in fosters adaptive thinking—a hallmark of elite security professionals. Users engage with gamified challenges that simulate real breaches, encouraging creative problem-solving and cross-tool coordination. These exercises reinforce pattern recognition, critical decision-making, and communication—skills indispensable in incident response teams.Moreover, the platform’s community features—such as shared test plans, peer reviews, and collaborative hackathons—create a dynamic learning ecosystem. As one user reflected, “Working through simulated attacks on HackingBot.in feels less like training and more like stepping into the discipline of a real security professional.”
Preparing for the Future of Ethical Hacking with HackingBot.in
As artificial intelligence and machine learning begin reshaping cybersecurity, ethical hacking tools must evolve in tandem. HackingBot.in stays ahead by integrating AI-driven anomaly detection, predictive risk modeling, and adaptive test automation—ensuring users remain front-runners in threat anticipation.“The future belongs to those who combine human intuition with algorithmic precision,” concludes领先 researcher Liu Wei. “HackingBot.in doesn’t just teach tools—it prepares testers for whatever tomorrow throws at them.”
For security professionals, researchers, and advocates alike, Exploring HackingBot.in: A Comprehensive Guide To Ethical Hacking Tools And Techniques reveals a platform built not just for exploitation, but for empowerment—a trusted ally in safeguarding our digital world through ethical, intelligent action.


Related Post

Deafness Unveiled: Separating Fact from Fiction Through the Insight of Sasaki Kojiro
No Nyt: Prepare to Question Every Moral Decision You’ve Ever Made, According to Kant’s Demanding Ethics
Mike Henry Actor Bio Wiki Age Height Wife Family Guy Smokey and the Bandit And Net Worth

