Master Cloud Computing with the 3-4-5 Rule: The Formula Empowering Scalable, Secure Deployment
Master Cloud Computing with the 3-4-5 Rule: The Formula Empowering Scalable, Secure Deployment
In an era defined by rapid digital transformation, cloud computing has evolved from a competitive advantage into an operational necessity. Organizations across industries rely on cloud platforms not only for data storage and application hosting but for agility, cost efficiency, and resilience. Yet, navigating the complexity of cloud environments demands structure—precisely where the 3-4-5 Rule emerges as a powerful framework.
By organizing cloud strategy into three strategic pillars and five operational best practices, this rule delivers clarity, consistency, and control, enabling businesses to scale securely and sustainably.
The 3-4-5 Rule distills the essential framework for effective cloud computing into three overarching domains: scalability, security, and governance. “Without a clear architecture spine,” notes enterprise cloud architect Dr.
Elena Torres, “organizations cloud-provide response but rarely resilience.” The Rule ensures that cloud transitions are not just technical migrations but holistic enterprise transformations rooted in measurable objectives.
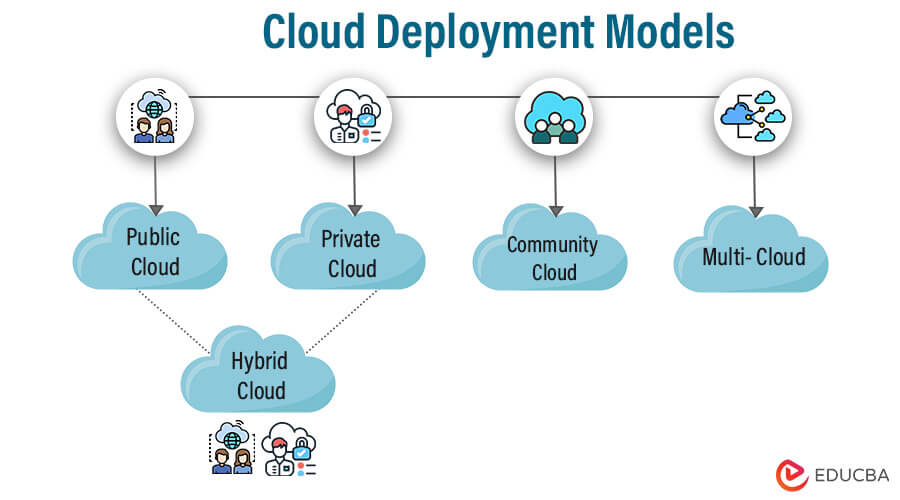
The 3 Core Pillars: Scalability, Security, and Governance
At its foundation, the 3-4-5 Rule rests on three non-negotiable pillars that define successful cloud adoption.- Scalability: Cloud environments must dynamically adapt to fluctuating demand, eliminating the rigid constraints of on-premises infrastructure. Whether supporting seasonal traffic spikes or long-term growth, businesses need cloud systems that scale seamlessly—automatically provisioning resources up or down with minimal latency.
This elasticity directly impacts performance, cost efficiency, and user satisfaction.
- Security: Protecting data and systems in shared, distributed environments is paramount. The Security pillar emphasizes rigorous access controls, encryption across all layers, and continuous threat monitoring. With cyberattacks growing in sophistication, a “set it and forget it” mentality fails—security must evolve in lockstep with cloud deployment.
- Governance: Without clear policies and oversight, cloud sprawl undermines accountability and compliance.
Governance ensures decisions align with business goals, regulatory requirements, and financial discipline. It establishes roles, enforces version control, and audits usage to prevent waste, duplication, and risk.
Five Actionable Best Practices: Implementing the 3-4-5 Rule Effectively
- Design for modular, microservices-based architecture: Decompose applications into independent services to enhance scalability and reduce deployment friction. Each module operates autonomously, enabling targeted scaling without system-wide rewrites.
- Enforce least-privilege access with automation: Use identity and access management (IAM) tools to assign minimal permissions dynamically. Automating provisioning and deprovisioning reduces human error, strengthens security, and maintains governance.
- Monitor consistently with real-time visibility: Deploy observability platforms that track performance, cost, and security across environments.
Automated alerts and dashboards empower teams to respond before issues escalate.
- Automate compliance checks and audits: Embed regulatory and security controls directly into CI/CD pipelines. Tools that validate configurations continuously prevent drift and ensure ongoing adherence to standards like GDPR or HIPAA.
- Plan for cost optimization at every stage: Use cloud



Related Post
Hulk Hogan Down for Potential Match with Randy Orton If He Wasnt Injured
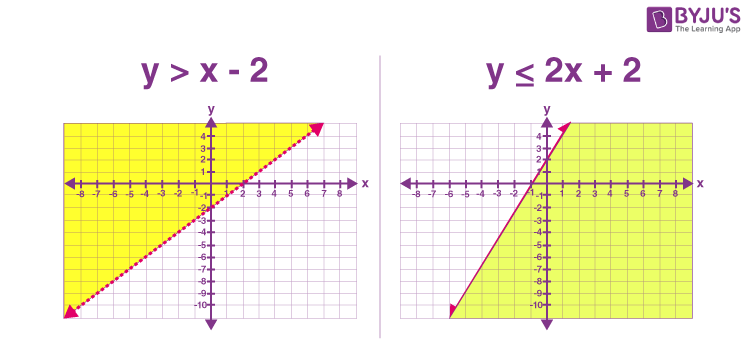
Mastering Linear Inequalities in Two Variables: The Essential Answer Guide from Lesson 7 3
Examining the Deep Impact of Eileen D. Medvey: A Objective Policy Examination

Amazon in Thailand: The Ultimate Shoppers’ Guide to Shopping with Confidence

