Unlock Seamless Access: Mastering Myrcc Login to Reclaim Your Digital Account
Unlock Seamless Access: Mastering Myrcc Login to Reclaim Your Digital Account
In a digital era where account security and instant access define user experience, the ability to log in securely and efficiently is non-negotiable—especially with platforms like Myrcc demanding precision and speed. The Myrcc Login Access Your Account process exemplifies this balance, offering a streamlined pathway to restore control over your digital identity. Whether you’re recovering a forgotten password or authenticating with multi-factor verification, this guide breaks down every critical step, challenge, and best practice to ensure your access is not only restored but fortified.
At the heart of Myrcc’s access protocol lies a user-centric design focused on both convenience and security. Logging in begins with a secure entry point: a clean, responsive interface optimized for desktop and mobile use. Users are greeted with fields for primary credentials—username or email and password—engineered to minimize input friction while enforcing robust encryption.
Fields are clearly labeled, with real-time validation preventing common errors before submission. Password entry is supported by secure masking, and password strengths are assessed dynamically to guide users toward stronger combinations. Biometric options—such as fingerprint or facial authentication—are available where supported, adding layers of effortless verification without compromising safety.
For enterprise-grade environments, Myrcc integrates federated identity protocols, enabling single sign-on (SSO) across trusted domains—eliminating repetitive logins without weakening security.
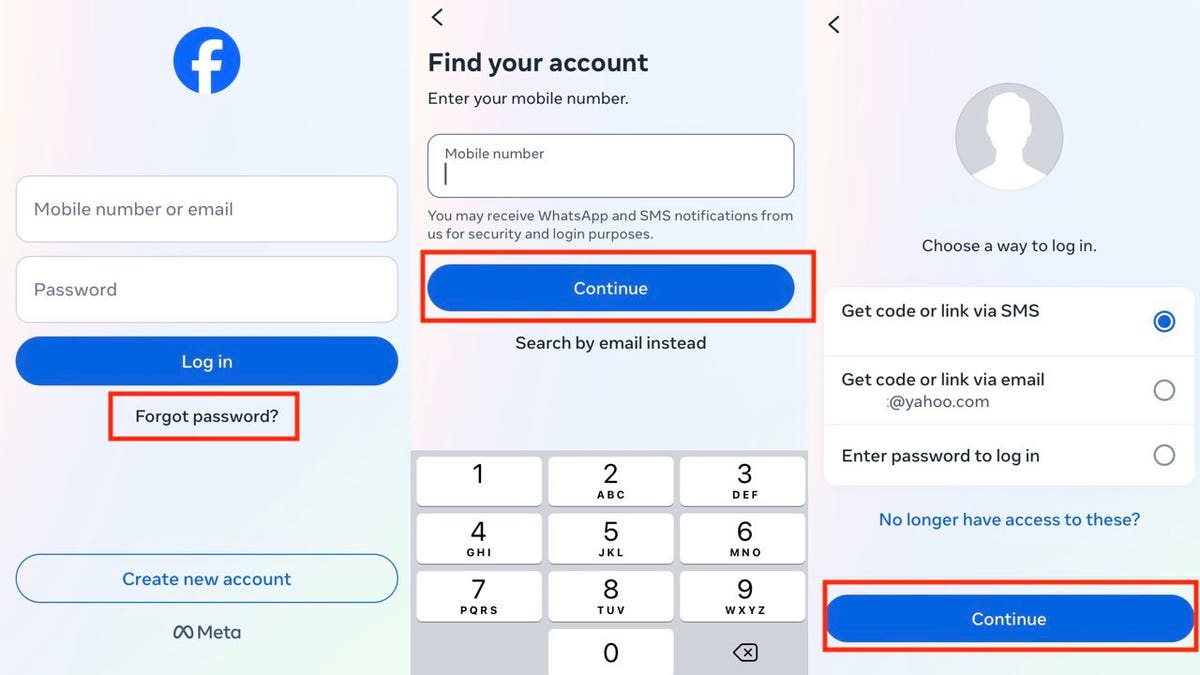
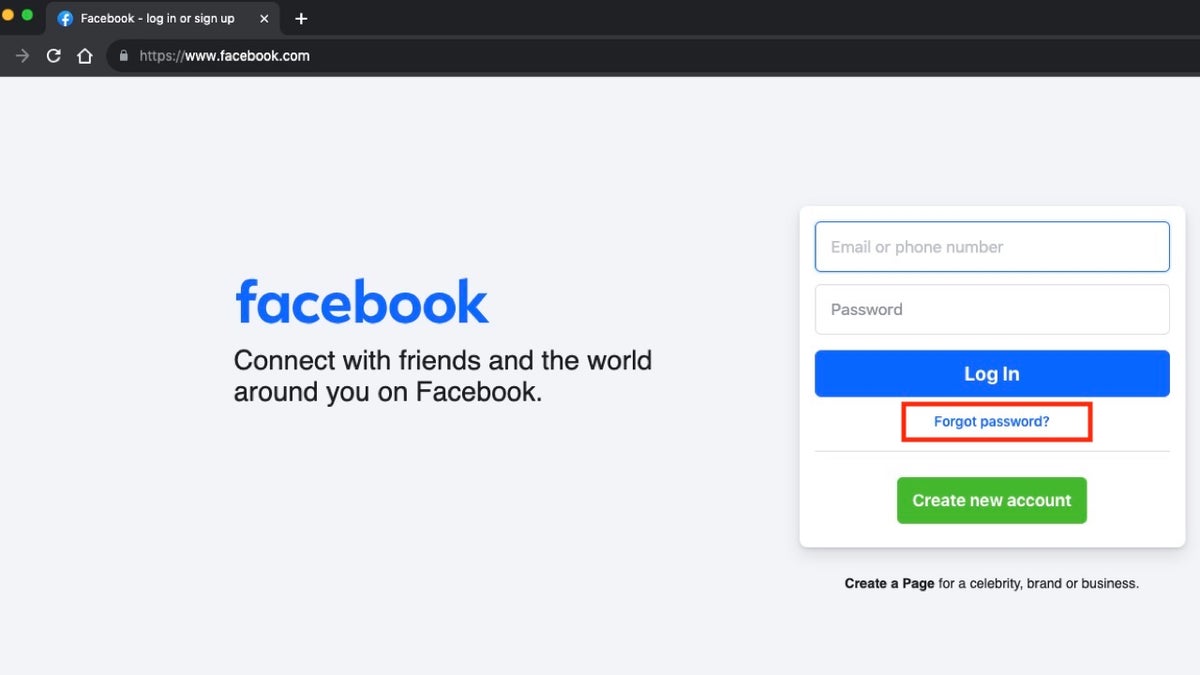
When traditional credentials fall short, Myrcc provides flexible recovery mechanisms. The “Forgot password?” option triggers a secure reset process, requiring identity verification through registered email, security questions, or out-of-band authentication codes. This layered approach—combining human-friendly prompts with backend rigor—ensures that even in failed login scenarios, users are never left locked out.
Security logs track every access attempt, delivering audit-ready transparency and enabling swift response to anomalies.
Strengthening Access: Multi-Factor Authentication & Risk-Based Verification
Security is not a one-size-fits-all solution, and Myrcc excels in adaptive authentication. Beyond basic password checks, the platform employs multi-factor authentication (MFA) as a cornerstone of account protection. Users can enable MFA via SMS codes, authenticator apps, hardware tokens, or biometric verification.“MFA transforms login from a single gate into a dynamic defense layer,” notes cybersecurity analyst Dr. Elena Torres. “Even if credentials are exposed, unauthorized access is thwarted by the second factor—making Myrcc a gold standard in identity safety.”
Risk-based authentication adds another dimension.
Myrcc’s smart system analyzes login behavior in real time—mapping typical geographic locations, device fingerprints, and usage patterns. A login from an unusual region or unfamiliar device may trigger additional verification steps, seamlessly balancing usability with enhanced security. This proactive stance reduces false positives while ensuring suspicious attempts are swiftly detected.
For enterprise clients, API-level integrations allow custom risk policies, aligning access control with organizational compliance frameworks.
Take Control: Steps to Access and Optimize Your Myrcc Account
Accessing your Myrcc account is structured for clarity and speed, but mastery comes from understanding its full ecosystem.- Begin at the official Myrcc login page, ensuring connection via HTTPS to prevent interception.
- Enter your registered email or username, then your password—utilize auto-complete where available for convenience.
- Upon submission, **do not** bypass verification: if prompted, complete MFA steps promptly.
- Post-login, review your dashboard immediately—this hub provides quick access to account settings, recent activity, and support links.
- For frequent users, generate long, unique passwords or consider integrating a password manager; enable MFA across all devices and accounts linked to Myrcc.
To maintain optimal access, regularly audit your account’s security settings. Myrcc allows users to revoke trusted devices, update recovery emails, and adjust notification preferences to stay ahead of potential threats.
For enterprises, Myrcc supports single sign-on (SSO) via SAML or OAuth, enabling centralized user management while preserving user experience.
Authentication logs are exportable and timestamped, offering audit trails critical for compliance with regulations like GDPR and HIPAA. Admins can enforce password policies, monitor login frequency, and deploy adaptive MFA based on user roles—ensuring enterprise-grade protection without user friction.
Real-World Use: Why Myrcc Login Resonates Across Industries
Myrcc’s login framework is purpose-built for environments where uptime and trust are paramount. In healthcare, secure patient data access prevents delays in care; in finance, frictionless yet secure authentication meets strict regulatory standards; in education, it supports scalable access for thousands of students and staff.The platform’s adaptability ensures it fits organizations of all sizes—from startups to global enterprises—without sacrificing the promise of robust identity verification.
As cyber threats evolve, so too do digital access protocols. Myrcc Login Access Your Account is more than a gateway—it’s a dynamic, evolving system ensuring users remain in control. Through intelligent design, adaptive security, and user-first principles, it demonstrates how access management can be both powerful and frictionless.
In a world of increasing digital complexity, the ability to authenticate swiftly and securely defines competitive advantage—and Myrcc delivers with clarity, strength, and precision.

Related Post

JaCoCo 3.5 Now Runs Flawlessly on Java 21: Master Lint-Driven Quality Today

From Dusty Plains to Sun-Scan Futures: How Oklahoma and California Reshape America’s Economic and Cultural Landscape

