Unlock Your IMEI Dial Codes: Access Contact and Device Secrets Instantly
Unlock Your IMEI Dial Codes: Access Contact and Device Secrets Instantly
Gaining instant access to your phone’s hidden dial codes through its IMEI number is no longer a technical mystery—it’s a practical tool for users, developers, and security-conscious individuals alike. The IMEI (International Mobile Equipment Identity) uniquely identifies every smartphone, enabling precise, code-driven interactions that streamline communication, system diagnostics, and app integrations. By learning to unlock and leverage these dial codes, users unlock a layer of efficiency and control previously confined to backend technical operations.
IMEI-based dial codes are standardized numeric sequences tied directly to a device’s hardware, making them reliable anchors for service access.
Each code corresponds to specific functions—connecting to operator portals, initiating emergency contacts, triggering automated support flows, or bypassing default access layers. “Dial codes embedded in IMEI data are the unsung gateways between users and their devices,” explains Dr. Elena Torres, a telecommunications security analyst.
“They offer a direct, low-latency pathway to precise device commands, bypassing the clutter of modern app menus.” These codes aren’t just technical artifacts; they empower seamless, secure, and rapid user interactions.
What Are IMEI Dial Codes? Background and Functionality
IMEI dial codes are predefined numerical sequences linked to a subscriber’s unique device identifier. When triggered through a call or app command, these codes initiate system-level responses—often bypassing standard user interfaces.Unlike customer service lines requiring authentication or lengthy verification, IMEI codes provide immediate, device-specific access, reducing friction across multiple use cases. Many mobile networks and OEMs embed these codes into diagnostic and provisioning protocols. For example, carrier systems often use IMEI dial codes to activate service plans, reset profiles, or reprogram network settings remotely.
Developers integrating with mobile devices also rely on these codes to trigger application behaviors tied to hardware identity, ensuring actions align precisely with the intended device. This standardization fosters interoperability across networks, apps, and support platforms.
Common Uses of IMEI Dial Codes in Practice
- Emergency Access: Dialing a specialized IMEI code routes emergency services directly to the device owner’s registered number, accelerating response times in critical situations.
- Service Provisioning: Operators use IMEI dial codes to remotely configure network settings, sync carrier profiles, or activate new SIM-based services without physical contact.
- Automated Diagnostics: Tech support platforms trigger diagnostic tools via IMEI codes, enabling real-time network health checks and firmware diagnostics.
- Device Management: Enterprise IT teams use IMEI codes to enforce security policies, remotely lock devices, or wipe data during asset loss or employee turnover.
- Custom App Integrations: Developers embed IMEI-code triggers into apps to deliver hardware-specific features—like hardware-based authentication or unique user preferences.
These applications demonstrate how IMEI dial codes serve as essential connectors between user intent and device capability.
By converting a device’s unique ID into an active command, they transform passive hardware into dynamic assets. This capability redefines accessibility—turning a static IMEI into a portal for instant, purpose-driven interaction.
The Mechanics: How IMEI Dial Codes Work Under the Hood
At their core, IMEI dial codes rely on preestablished mappings between a device’s ID and its active function. When a call tapped to a registered IMEI dial code, the network or system interprets the sequence as a directive.The activation process typically involves:
- Device Validation: The system verifies the IMEI’s authenticity against carrier or OEM databases.
- Code Execution: Predefined commands—network reconfiguration, contact routing, or diagnostic launches—are triggered instantly.
- Secure Response: The device replies with a status acknowledgment, confirming action completion or failure.
Enhancing Security and Compliance with IMEI Dial Codes
Using IMEI dial codes isn’t just convenient—it’s also a strategic approach to securing communications and enforcing accountability. Because each code is permanently linked to a specific hardware unit, unauthorized access attempts are immediately traceable to the device, enabling precise logging and policy enforcement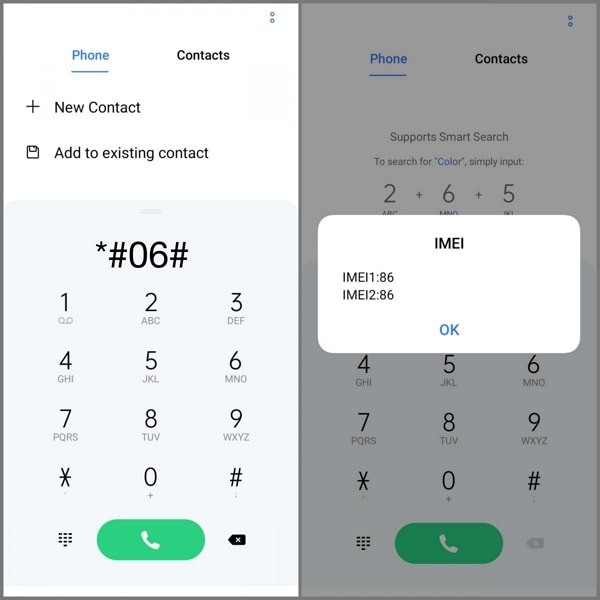
![[ 2025 ] How to Get IMEI Number on iPhone if Locked? 7 Ways!](https://images.wootechy.com/article/find-imei-number-by-dialing-code.png)


Related Post
Cane Masters The Secret Weapon That Can Give You Superhuman Strength

Unlocking Excel That Works: How Gianteagle Com Enroll Transforms Learning and Enrollment Management

Chris Forsberg’s Wife: Behind the Gym Star’s Private Life Over the Spotlight

WhatIsAPatriot: More Than a Name—A Living Legacy of Service and Identity

