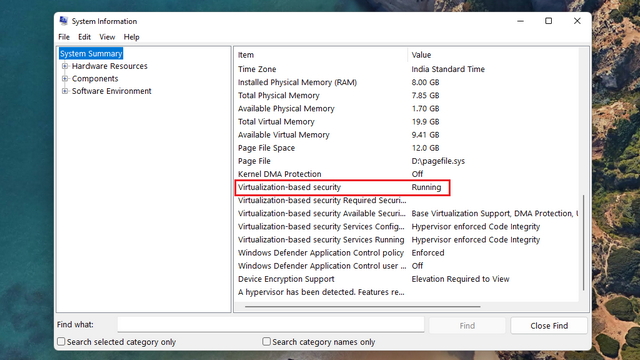
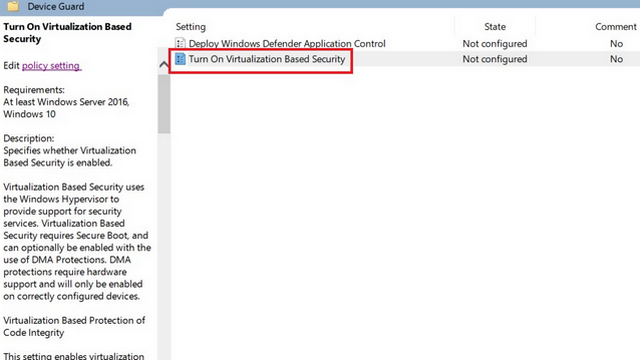
Virtualization-Based Security (VBS): A Deep Dive into Modern Enterprise Protection
Virtualization-Based Security (VBS): A Deep Dive into Modern Enterprise Protection
At the edge of modern computing’s most critical security frontier lies Virtualization-Based Security—VBS—a transformative technology reshaping how organizations defend against advanced threats. By leveraging hardware-enforced isolation through virtualization, VBS creates secure containers within legitimate operating system environments, rendering many traditional attack vectors obsolete. This deep dive explores how VBS operates, its architectural foundations, real-world deployment, and the profound implications for securing today’s dynamic digital infrastructures.
Virtualization-Based Security is not merely a new software layer; it is a fundamental shift in protection philosophy, built upon the principle that security should be woven into the platform’s core. By embedding security controls directly into the virtualization layer, VBS enables the creation of validated execution environments—often referred to as “secure enclaves”—that isolate critical processes from potential compromise. These enclaves run with strict separation from untrusted system components, significantly reducing attack surfaces.
The Architectural Foundation of VBS: How Virtualization Enables Security
VBS relies on a core technology rooted in Microsoft’s Windows Defender Application Guard and Hyper-V integration.At its heart is the Virtualization Priority Service (VPS), a hypervisor-level driver that enforces mandatory virtualization policies. These policies stipulate that only verified, security-critical processes execute within isolated virtual machines (VMs), while the host and non-secure guest operating systems remain outside this protected boundary.
- VBS utilizes Nested Virtualization to build secure containers within trusted VMs, preventing attackers from breaching protective layers.
- It leverages Protected Process Linking (PPL) to bind system-critical binaries to secure enclaves, ensuring their integrity and authenticity.
- Secure Boot and Credential Enrollment (using TPM 2.0) authenticate device hardware before VBS initializes, forming a chain of trust from firmware to application.
- The Secure Configuration Manager enforces hardened, immutable setups, minimizing configuration drift and vulnerability exposure.
The strength of VBS lies in its hardware-assisted trust model.
Unlike software-only antiviruses or perimeter firewalls, VBS leverages CPU features—such as Intel VT-d and AMD-Vi—to enforce memory isolation and protect sensitive data from unauthorized access. This hardware-backed isolation ensures that even if an adversary compromises an application or service, the damage is confined within a VBS container, preventing lateral movement across the system.
Real-World Deployment: From Enterprise Data Centers to Cloud Environments
Organizations across finance, healthcare, and government sectors are adopting VBS to protect high-value systems. In data centers, VBS hardens virtualized workloads—critical for cloud providers managing multi-tenant environments—by isolating enterprise applications from untrusted guest or service processes.Financial institutions, for example, deploy VBS to secure transaction processing environments, preventing malware from intercepting sensitive data during high-risk operations.
Cloud providers integrate VBS into container orchestration platforms, enhancing Kubernetes clusters by enforcing secure, isolated execution of microservices. This prevents supply chain attacks and runtime compromise, critical for maintaining compliance with regulations like GDPR and HIPAA.
The ability of VBS to superimpose defensible security boundaries atop commodity virtualization makes it uniquely suited for complex, scalable infrastructures.
Use Cases That Transform Security Posture
- **Secure Boot & Kernel Isolation:** VBS enables runtime verification of kernel modules, blocking unauthorized kernel-level code execution. - **Protected Remote Desktop:** Virtualized Remote Desktop sessions run inside encrypted VMs, shielding credentials and desktop environments from keyloggers and screen scrapers. - **Hardware-Accelerated Encryption:** Secure enclaves store cryptographic keys and perform sensitive operations in isolated VMs, preventing extraction via memory scraping attacks.- **Zero Trust Networking:** Combined with software-defined networking, VBS ensures every virtualized component authenticates and encrypts traffic at the process level.
These use cases exemplify VBS’s role not as a standalone product, but as a foundational pillar of a layered security strategy. By embedding trust at the virtualization layer, it enables consistent, enforceable protection without sacrificing performance or operational agility.
Challenges and Considerations in VBS Implementation
Despite its robust security model, successful VBS deployment requires careful planning.Legacy systems may resist VBS integration due to compatibility constraints with older drivers or workflows. Administrators must also reconcile VBS isolation policies with business needs—overly restrictive configurations can disrupt legitimate service dependencies in containerized or microservice architectures.
Performance overhead remains a topic of scrutiny.
While modern CPUs minimize latency through hardware-assisted virtualization, large-scale deployments—especially in high-performance computing or real-time analytics—demand benchmarking and optimization to maintain acceptable throughput. Nonetheless, documented performance impacts are often negligible compared to the security gains achieved by isolating critical assets.
Future Trajectory: VBS in the Age of Zero Trust and Emerging Threats
As cyber threats evolve—from hardware-based attacks to supply chain compromises—VBS is poised to become a cornerstone of next-generation security frameworks. Its convergence with Zero Trust Architecture amplifies protection by verifying every access request within secure execution environments.Moreover, advancements in confidential computing—where data remains encrypted in use—extend VBS’s capabilities, enabling secure data processing across untrusted clouds.
Industry experts emphasize that VBS is no longer optional for enterprises prioritizing cyber resilience. Its ability to protect systems from both inside and outside threats, while preserving operational efficiency, positions it as indispensable in safeguarding the digital backbone of global organizations.
As virtualization technologies mature and expand into hardware-verified secure enclaves beyond x86 platforms, VBS will continue redefining how security is engineered at the system level.
Virtualization-Based Security represents more than a technical innovation—it is a paradigm shift in defending critical infrastructure. By anchoring security in virtualization and hardware trust, VBS delivers a powerful, scalable defense against modern threats, proving that the future of cybersecurity lies in embedding protection into the very fabric of computing platforms.


Related Post
Sean McLaughlin CBS 5 Bio Wiki Age Wife Salary and Net Worth
Finding Elegance in Grief: The Story of Elmwood Funeral Home in Abilene, Texas

Kamala Harris: A Political Beacon and Her Spouse’s Quiet Influence Behind the Net Worth Figure
Saint Seiya: The 12 Houses – Unlocking the Cosmic Blueprint of the Warriors

